Getty Photos
Researchers have devised a low-cost smartphone assault that cracks the authentication fingerprint used to unlock the display screen and carry out different delicate actions on a spread of Android gadgets in as little as 45 minutes.
Dubbed BrutePrint by its creators, the assault requires an adversary to have bodily management of a tool when it’s misplaced, stolen, quickly surrendered, or unattended, for example, whereas the proprietor is asleep. The target: to achieve the power to carry out a brute-force assault that tries enormous numbers of fingerprint guesses till one is discovered that can unlock the gadget. The assault exploits vulnerabilities and weaknesses within the gadget SFA (smartphone fingerprint authentication).
BrutePrint overview
BrutePrint is an affordable assault that exploits vulnerabilities that permit folks to unlock gadgets by exploiting numerous vulnerabilities and weaknesses in smartphone fingerprint authentication programs. Right here’s the workflow of those programs, that are sometimes abbreviated as SFAs.
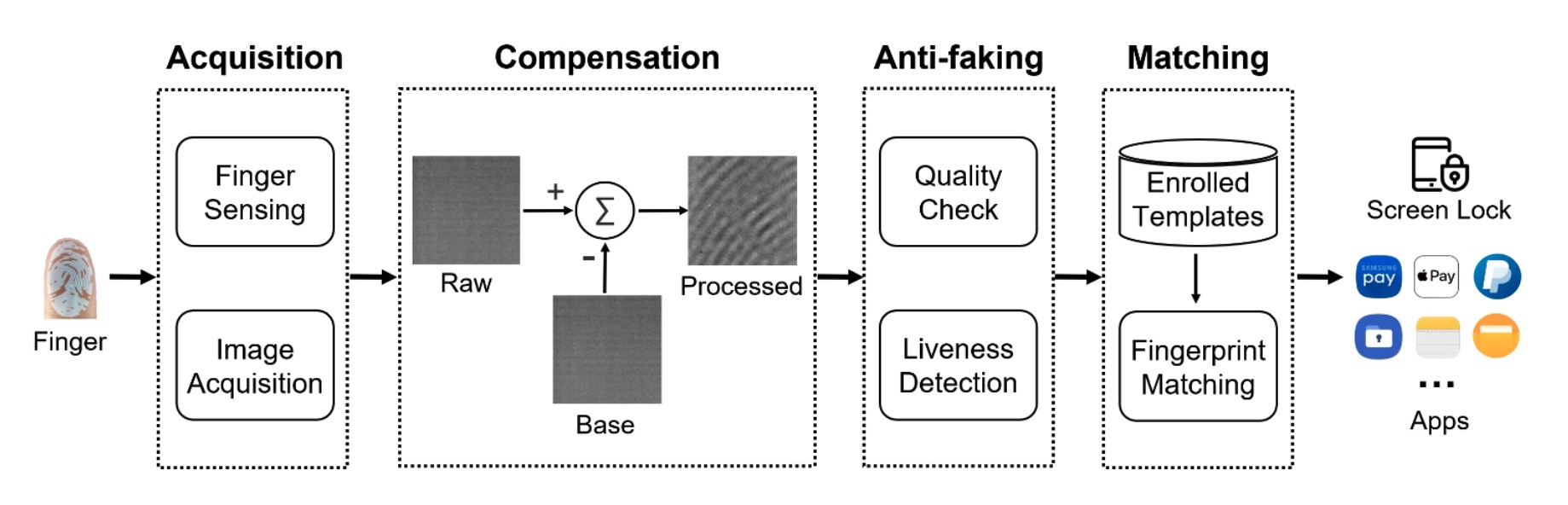
The workflow of a smartphone fingerprint authentication system.
The core of the gear required for BrutePrint is a $15 circuit board that accommodates (1) an STM32F412 microcontroller from STMicroelectronics, (2) a bidirectional, dual-channel, analog swap referred to as an RS2117, (3) an SD flash card with 8GB of reminiscence, and (4) a board-to-board connector that connects to the cellphone motherboard to the fingerprint versatile printed circuit of the fingerprint sensor.
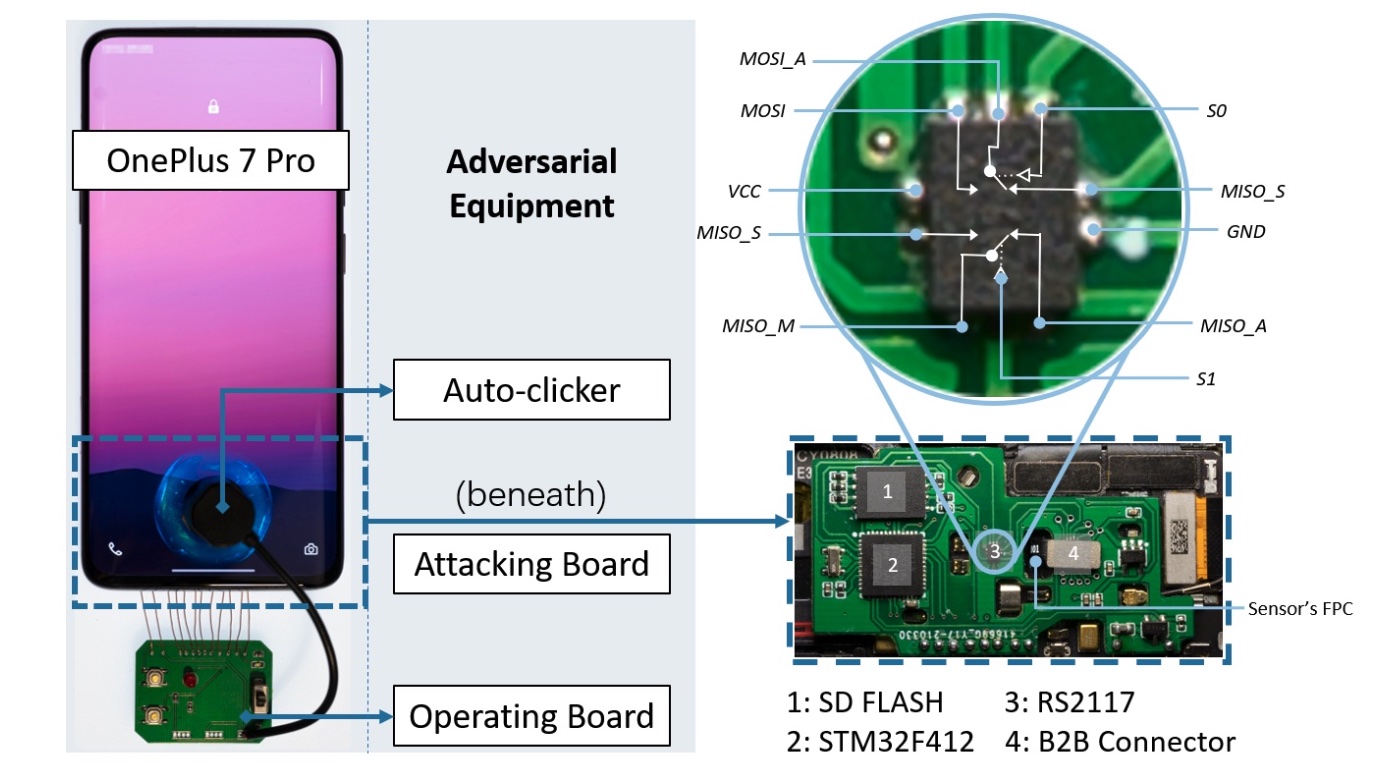
The adversary gadget that varieties the core of the BrutePrint assault.
Moreover, the assault requires a database of fingerprints, much like these utilized in analysis or leaked in real-world breaches akin to these.
Commercial
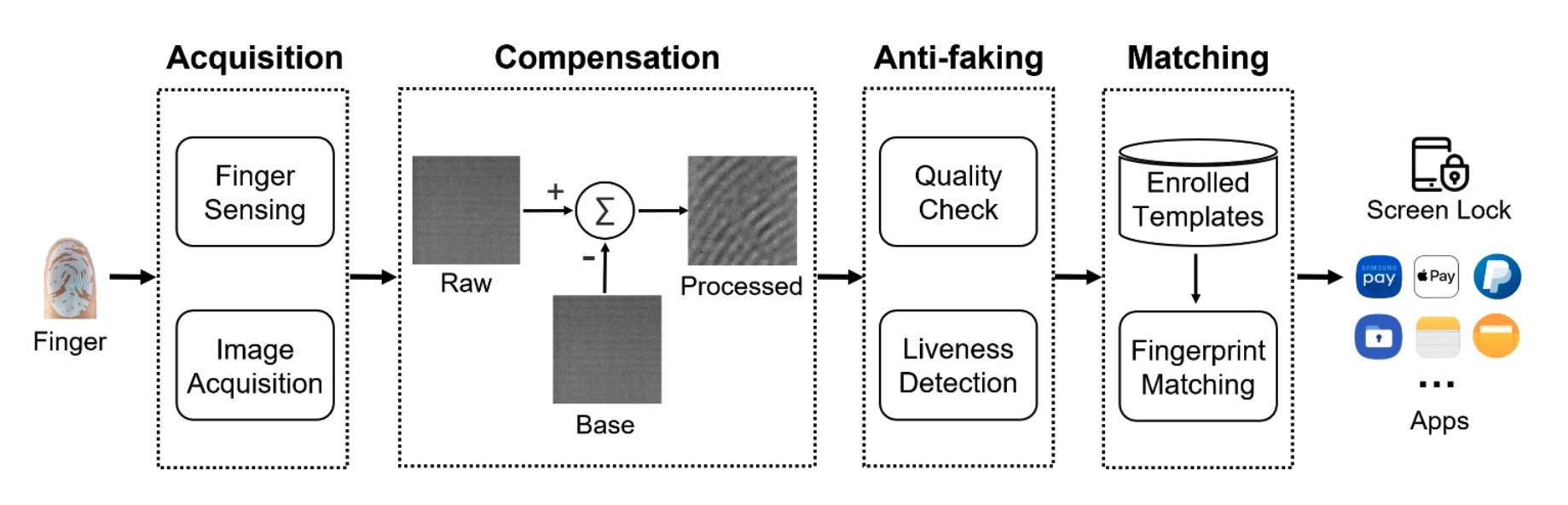
An summary of the BrutePrint assault.
Not all smartphones are created equal
Extra on how BrutePrint works later. First, a breakdown of how numerous cellphone fashions fared. In all, the researchers examined 10 fashions: Xiaomi Mi 11 Extremely, Vivo X60 Professional, OnePlus 7 Professional, OPPO Reno Ace, Samsung Galaxy S10+, OnePlus 5T, Huawei Mate30 Professional 5G, Huawei P40, Apple iPhone SE, Apple iPhone 7.
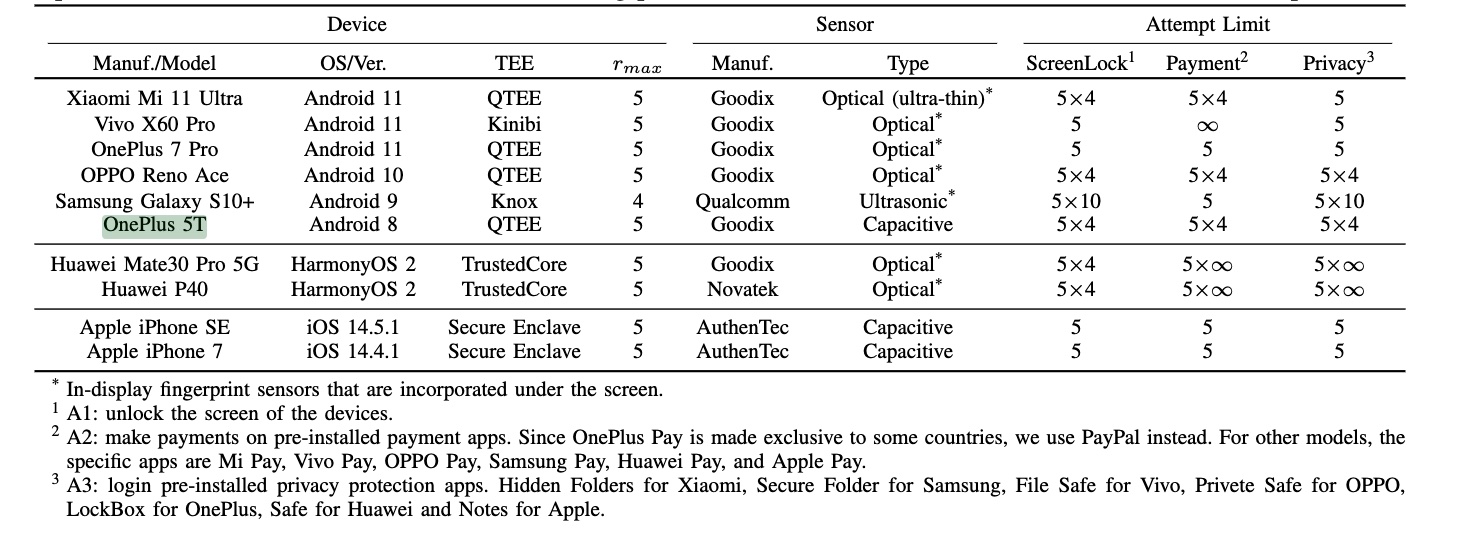
An inventory of the gadgets examined together with numerous attributes of the gadgets.
The researchers examined every for numerous vulnerabilities, weaknesses, or susceptibility to numerous assault strategies. Examined attributes included the variety of samples in multi-sampling, the existence of error-cancel, help for hot-plugging, whether or not information might be decoded, and information transmission frequency on SPI. Moreover, the researchers examined three assaults: tried restrict bypassing, hijacking of fingerprint pictures, and fingerprint brute-forcing.
Outcomes of varied assaults on the completely different gadgets examined.
Final, the researchers offered outcomes exhibiting the time it took for numerous telephones to have their fingerprints brute-forced. As a result of the period of time is dependent upon the variety of prints approved, the researchers set every to a single print.
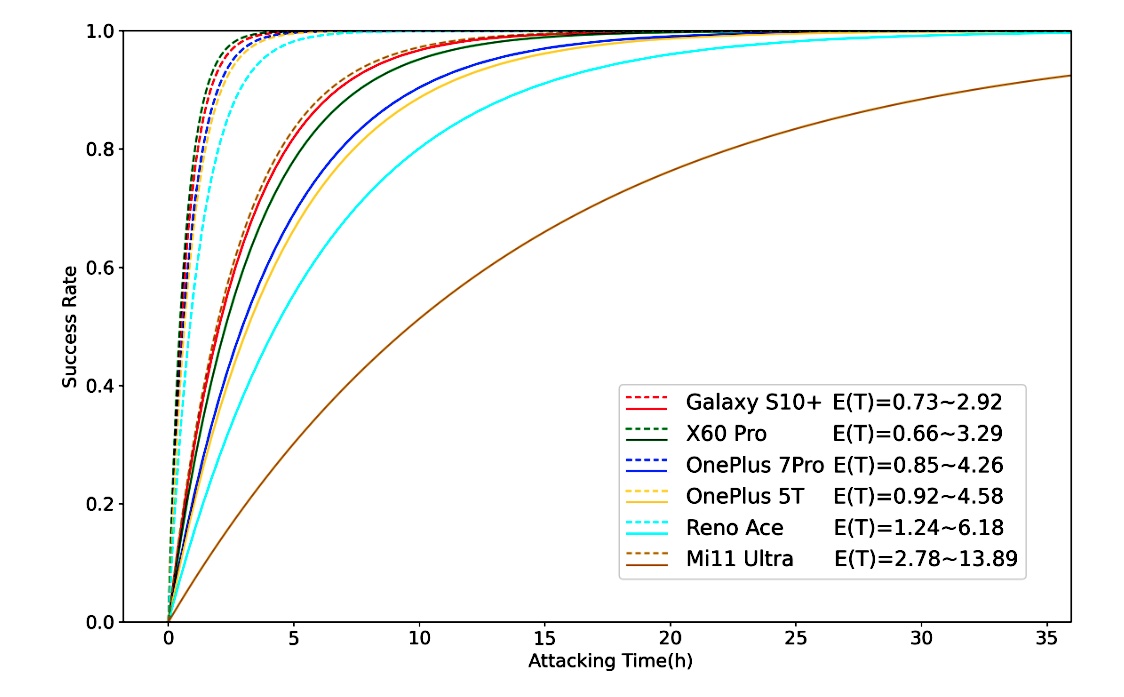
The success price of varied gadgets examined, with the Galaxy S10+ taking the least period of time (0.73 to 2.9 hours) and the Mi11 taking the longest (2.78 to 13.89 hours).
Though specifics diversified, the result’s that BrutePrint can try a vast variety of authentication fingerprints on all eight of the Android fashions examined. Relying on numerous components, together with the fingerprint authentication framework of a selected cellphone and the variety of fingerprints saved for authentication, it takes anyplace from about 40 minutes to 14 hours.